No ivory that is not cracked. That proverb is right for unmanned fighter aircraft technology the United States. Advanced fighter aircraft, unmanned remotely controlled or drone, used in the United States reconnaissance and attack missions in the war was easily sabotaged.
 |
| Drones are mostly used for military operations. (Picture from: http://www.bbc.co.uk/) |
The team of scientists that serve the challenges of the U.S. Department of Homeland Security (DHS) in mengulik weakness of drones. Todd Humphreys and a team of Radio Navigation Laboratory indicate the "spoofing" method in front of DHS officials. He uses a plane-sized unmanned mini helicopter that was flown over the stadium in the City of Austin.
Humphreys managed to hijack a GPS system drone university. Control of unmanned aircraft can be taken over after the aircraft GPS system is compromised and manipulated.
 |
| How drones.work. (Picture from: http://www.bbc.co.uk/) |
The U.S. military now often use this multifunctional drone because it can be controlled from a central headquarters are located thousands of kilometers away. Drones are often deployed in conflict zones like Afghanistan and Pakistan.
Military analysts said the "spoofing" method demo is displayed by Humphreys shows the potential hazards of the use of drones in the military mission. This method was allegedly used to bring down a U.S. military drone in Iran in 2011.
Noel Sharkey, founder of the International Committee for Robot Arms Control, said the "spoofing" method utilizing GPS signals are not encrypted. This signal is typically used civil aircraft.
"It's easy to fool an unencrypted signals from unmanned aircraft," said Sharkey. He added that anyone who is skilled can do and only requires equipment worth U.S. $ 1,000.
Sabotage drone with the method of "spoofing" proved to be very effective and dangerous. Sharkey said a hijacker can make drones as if "thinking" sliding into a specified location of the military headquarters. Though the plane was shot to another location that has been determined by hijackers.
The hijackers also can cripple drone, stealing, and filled it with explosives and pointed it somewhere else. "It becomes very dangerous because they can change direction and launched at the innocent peoples," said Sharkey. *** [FOXNEWS | MAHARDIKA SATRIA HADI | KORAN TEMPO 3928]

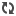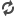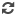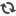 Logging you in...
Logging you in...